Pratical Malware Analysis #1 Pages 1-20
Published:
What is covered
- Pages 1-10 a brief into into different malware types (not covered too much here)
- Pages 10-20 begining to understand malware and how to reverse it what tools to use etc
Pages 10-15
Discussed first is the different types of tools used for static analysis, this book is fairly old so I'll update some tools mentioned to my preferred alternatives. Firstly discussed, is antivirus to be used for malware scanning to better understand the program, e.g. virus total, pretty basic and well known, use this tool to better understand what your malware does without doing much work at all, also used for testing your own malware to see if it can be detected.
Next talked about is malware hashing, a hash is a fingerprint to identify anything, not just malware. Nowadays this alomng with signature based detection is not as effective as malware can just be packed so easily, changing both the file hash / signature.
The book further talks about string detection, for this essentially any program can be used IDA, Windbg etc. You don't necessarily need a specific application to show an apps strings anymore. Something I didn't know, ASCII and unicode strings are null terminated, meaning there is a null byte at the end of every string, to mark its end. Mentions how strings may be used to determine what type of malware the program is, e.g. via function names or error codes e.g. a mailing system error code.
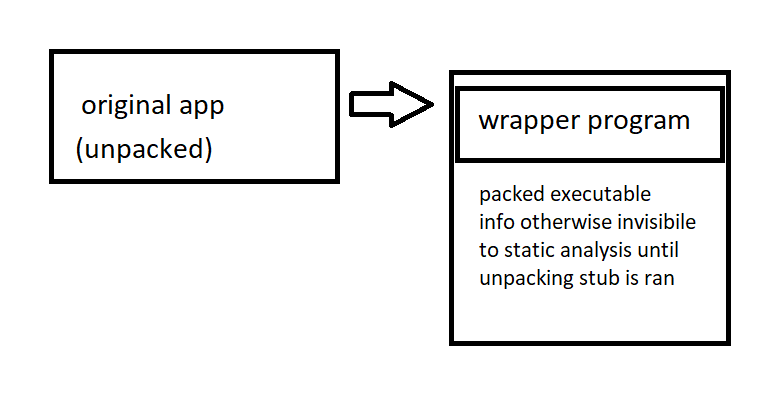
Packing and obfuscation
Packed malware can easily be identified just by viewing an apps strings, if they're gibberish then you kmow it's packed. To find which pakcer has been used, this tool can be used.
Pages 15-20
Linked libraries
Briefly discuesses windows PE format but nothing of importance. Mentions how a programs imports can show a lot about tis functionality, function imports are necessary and almost all windows programs will import kernel32.dll to perform even the most basic of tasks.
Static vs dynamic linking
- Static linking means all the code in the linked library is available inside the executable at compilation
- This makes the filesize larger and easier to idenfity a programs imports
- Tip the book mentions that functions can also be imported via ordinal not name - making the analysis harder as the ordinal number is less identifiable rather than a string
Dynamic linking means the functions are imported at runtime whether that is via LoadLibrary or GetProcAddress
This makes static analysis more difficult especially for automated tools which can't simply read which imports are being made through the import table anymore
The important part of library linking are the functions imported e.g. URLDownloadToFile - I wonder what this does
Pe bear can show a programs imports
Dependency walker shows all dynamically linked functions of a pe file
Exported functions
The book explains how DLLs are typically the only files which contain exported functions as these are used to provide functionality to executable files. Not being very common, exported functions can be a good indicator of what a program may wish to do.
Clever Example
In windows for an application to be ran as a service the ServiceMain function must be defined. Therefore, if an executable (e.g. your malware) has an exported function called "ServiceMain", the malware is trying to install itself as a service. This is if the malware chooses to use the same naming convention as mirosoft doumentation which it most likely will not, meaning this can be used to mislead analysts / just obfuscated the exported names.
Keylogger executable analysis
The books uses an example of a keylogger in regards to what imports it is makeing, these imports were all clearly visible from dependency walker, so it's assumed the malware was not packed. I've reconstructed below the imports the exec is making, and what we can assume from them.

As you can see from the imported functions above, some are very interesting and tell us directly that this program is suspicious
Kernel32.dll
- OpenProcess / other functions can tell use this app can manipulate other processes
- Readfile / io functions tell us that this program can search directories / files
User32.dll
- Setwindowshookex if the program is suspected malware and this function is seen it's likely that this is some sort of keylogging functionality
Exports
LowLevelKeyboardProc - callback function used with SetWIndowsHookEx to specify which function inside the program will be called on a given event
With all the above information, it's safe to assume that this program attempts to read the users input
All in all this book is begining to be a fun read and very interesting, in my next post I'll be reading pages 20-40 and most likely making some more detailed notes.